When deploying applications through Microsoft Intune, one of the key challenges is ensuring that apps get detected as installed after a successful installation – or worse, that failed installations don’t go unnoticed..
That’s where detection rules come in. These rules check whether an application is already present on a device.
Setting up detection rules in Intune might seem a little overwhelming at first, but don’t worry—we’ll walk you through it step by step.
In this guide, we’ll break down how detection rules work, walk you through setting them up in Intune, and show you how PacKit makes the process even easier.
What Are Detection Rules and How Do They Work?
In Microsoft Intune, detection rules are used to verify the presence of a Win32 application on a device. These rules ensure that the application installation process is triggered only if the application is not already installed. Additionally, they help confirm whether the installation was successful.
How to Set Up Detection Rules in Intune?
When configuring detection rules in Intune, you need to specify how the presence of the application will be detected.
Go to the Detection rules pane -> Rules format. There, you can choose between the following rule formats:
You can choose between:
- Manually configure detection rules
- Use a custom detection script
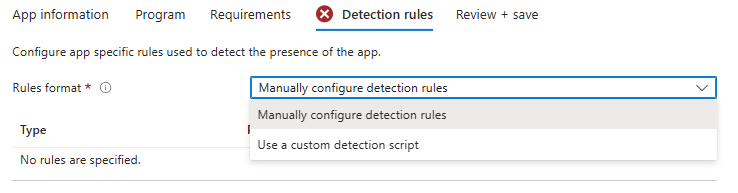
Manually Configure Detection Rules
If you choose to manually configure detection rules, you can select one or more of the following rule types:
- MSI
- File
- Registry
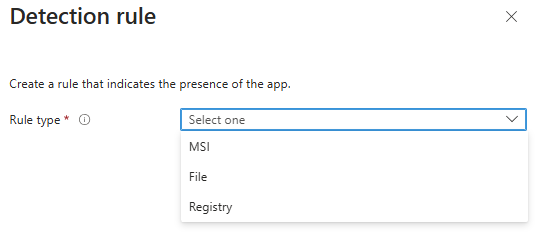
1. MSI – Detect Based on MSI Product Code
This rule verifies the application using the MSI Product Code. It can only be added once.
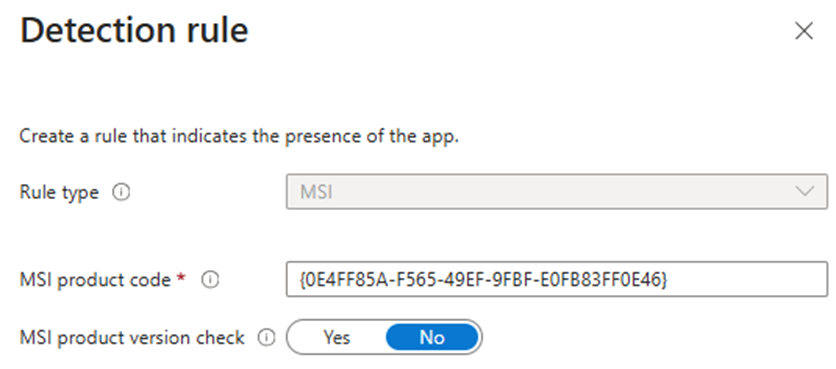
- MSI Product Code – Defines a valid MSI product code for the application.
- MSI Product Version Check – Verifies the MSI product version in addition to the MSI product code.
For MSI packages, using the MSI Rule Type is recommended.
2. File – Detect Based on File or Folder
This rule verifies the presence of a specific file or folder.
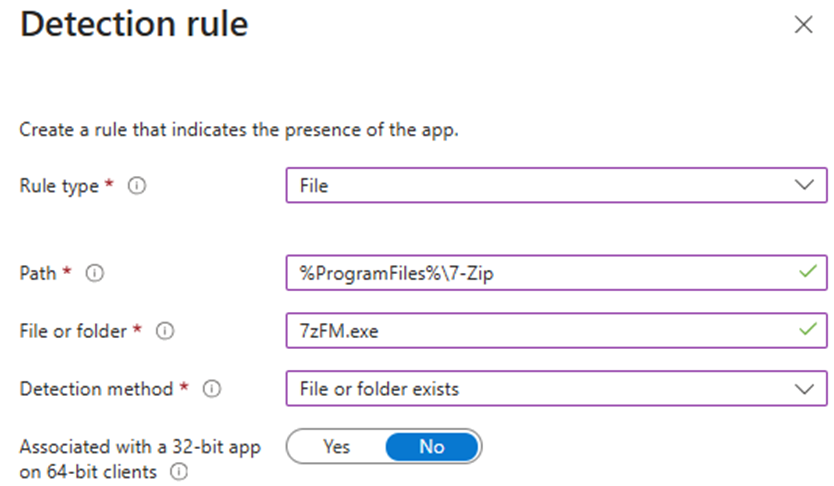
- Path – Defines the full path of the folder containing the file or folder to detect.
- File or Folder – Specifies the file or folder to detect
- Detection Method – Defines the type of detection method used to detect the presence of the app:
- File or folder exists
- Date modified
- Date Created
- String (version)
- Size in MB
- Associated with a 32-bit app on 64-bit clients – Expands path environment variables in 32-bit context on 64-bit clients.
3. Registry – Detect Based on Registry Key Path or Value
This rule verifies the presence of an application using the Windows registry.
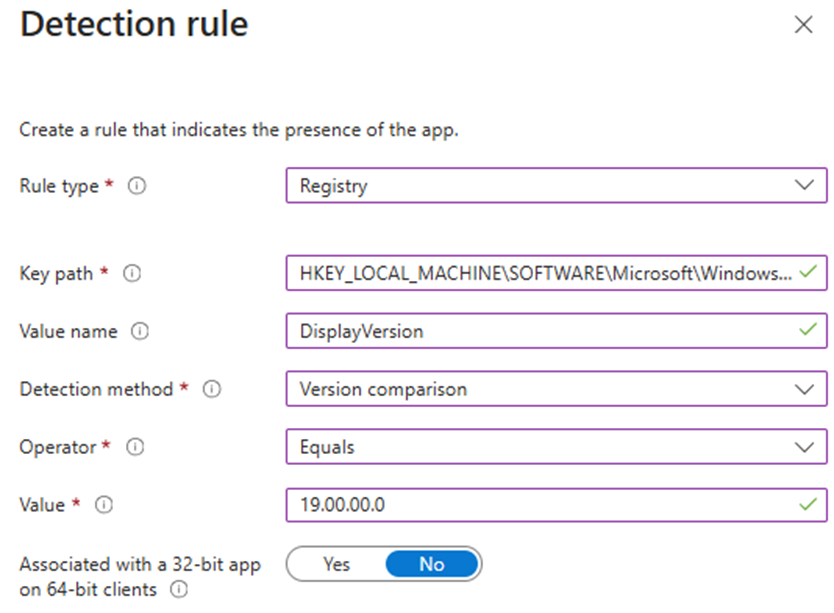
- Key Path – Defines the full path of the registry key that contains the value to detect
- Value Name – Specifies the name of the registry value to detect.
- Detection Method – Determines the type of the detection method used to detect the presence of the app:
- Key exists
- Key does not exist
- String comparison
- Version comparison
- Integer comparison
- Associated with a 32-bit app on 64-bit clients – Searches the 32-bit registry on 64-bit clients.
Use a Custom Detection Script
If you choose the custom detection script option, you can specify a PowerShell script to detect the presence of the application. The application will be considered detected if the script:
- Returns an exit code of 0.
- Writes a string value to STDOUT.
For more details on adding and configuring App Detection Rule in Intune, you can check out Add and assign Win32 apps to Microsoft Intune | Microsoft Learn
Setting an App Detection Rule Using PacKit
To set up a Detection Rule in PacKit, follow these steps:
- Navigate to the Package Information pane.
- Locate the Detection Method section.
- Select the most appropriate Detection Rule for your application.
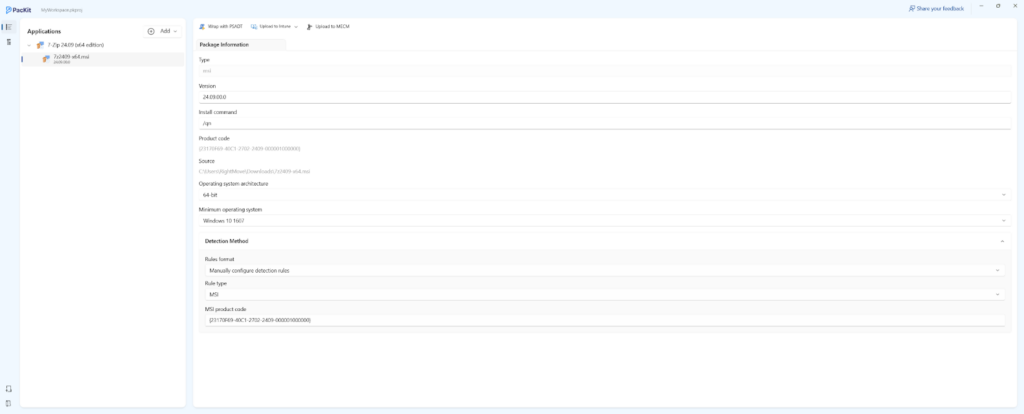
The available options and setup processes in PacKit are similar to those in Intune.
If you choose MSI Rule Type (and your package is in MSI format), the Product Code field is automatically pre-populated with the MSI’s Product Code.
PacKit streamlines application packaging and deployment by automating detection rule configuration and integrating seamlessly with Intune.Try it today!
Conclusion
Configuring an App Detection Rule in PacKit is straightforward and user-friendly. Once set up, the Detection Rule within PacKit will be used when uploading the package to Intune, ensuring a seamless integration.
FAQ
What is the purpose of an App Detection Rule in Intune?
An App Detection Rule ensures that a Win32 application is only installed if it is not already present on the device. It also helps verify whether the installation was successful.
Which detection rule should I use for an MSI package?
For MSI packages, it is recommended to use the MSI Rule Type, as it directly verifies the MSI Product Code and version.
Can I use multiple detection rules for the same application?
Yes, you can combine different detection methods (MSI, File, Registry) for more accurate detection. However, only one MSI rule can be added per application.
How does a custom detection script work?
A custom detection script uses PowerShell to check for the application’s presence. The script must return an exit code of 0 and write a string value to STDOUT for the application to be detected.
Does PacKit support all the detection methods available in Intune?
Yes, PacKit supports the same detection methods as Intune, allowing seamless configuration and integration.